Cybersecurity Tips: Protect Yourself Online
The rapid growth and widening of technology has certainly made our lives easier in many respects. Once-dreamed-of luxuries now seem like second nature. We can connect with loved ones across the globe through video calls, access endless entertainment from the comfort of our couch, and manage everyday tasks like banking and shopping without ever stepping outside of our home.
However, with these conveniences come new challenges – especially when it comes to protecting yourself online. Cybercriminals are always looking for new ways to take advantage of unsuspecting internet users, but by implementing a few simple practices, you can protect yourself and your family, and enjoy all the benefits of modern technology with peace of mind.
According to Bloomberg, at $9.5 trillion, cybercrime is the third largest economy in the world, following only the United States and China. Populated by bad actors, the World Economic Forum describes it as the “dark underbelly of the digital era.” Data breaches cost businesses an average of $4.88 million in 2024. 53.55 million Americans were affected by cybercrime in the first half of 2022. 1 in 2 American internet users had their accounts breached in 2021.
These figures are astonishing and can seem daunting for those of us that use the internet for almost everything, but there is hope. Cybersecurity experts say there are a few, simple measures you can put in place that dramatically decrease your chances of becoming a victim of cybercrime. Whether you’re checking your email, shopping for a gift, or keeping up with friends on social media, these practical guidelines will help keep your personal information secure.
Use Strong, Unique Passwords:
- Experts say that maintaining strong, unique passwords is the easiest and most effective way to ensure the security of your accounts online. While they are easier to remember, simple passwords like "password123" or "john9185" can easily be guessed using simple account information, like your name and birthday, that hackers likely already have. Combining uppercase and lowercase letters, numbers, and symbols can dramatically increase the strength of your passwords.
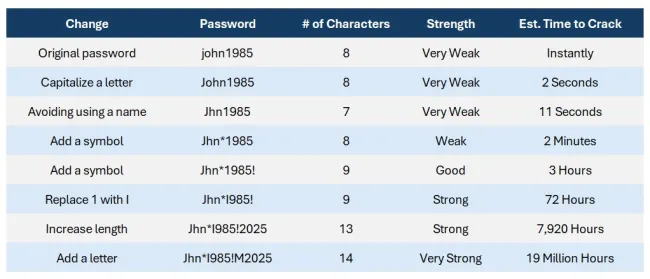
- There are a few characteristics of passwords that weaken them: short length, predictable patterns (e.g. "12345" or "qwerty"), simple words like "password" or "letmein", using your name, birthday, or username. To create strong passwords, use a mix of of character types, avoid predictable patterns, and aim for at least 12-16 characters.
- Password strength is measured by the length of time it would take a computer to crack your password by brute strength - essentially, how long would it take a computer to guess your password? Below, you'll find variations of a relatively simple base password and their respective strengths according to PasswordMonster:
Use a Password Manager:
- Password managers like Keeper and BitWarden are worth their weight in gold in the digital era. Not only will they store your username and password information for all your accounts, they will also help you generate new passwords in place of the ones they deem to be weak. No more 5-page binder of usernames and passwords - simply remember your master password and the answer to a few security questions and you are all set.
Use Two-Factor/Multi-Factor Authentication (2FA/MFA):
- Whenever possible, turn on 2FA/MFA, especially for accounts like online banking and email. With this option enabled, any login attempt will require authentication on another device, typically your phone. Giving you the ability to reject uninitiated login attempts, this adds another layer of protection.
Utilize Biometrics Whenever Possible:
- Biometrics are physical or behavioral characteristics, such as fingerprints, facial recognition, or voice patterns, used to verify a person's identity. They play a crucial role in your personal cybersecurity by providing a unique and difficult-to-replicate layer of authentication. As digital threats grow, biometrics are becoming essential for enhancing identity protection.
Beware of Phishing Scams:
- Never click on links or open attachments from unexpected emails or texts, especially if they claim to be urgent. Banks and government agencies will never ask for your password via email, and they will certainly never ask you to pay for anything using gift cards.
- Email addresses you receive emails from can oftentimes clue you into these scams. For example: a legitimate email from Netflix regarding your account information is most likely going to come from info@account.netflix.com, according to their website. If you receive an email that looks official, but originated from info@acount.netfllix.en-us (misspelled and strange domain name), that is more than likely a scam and should be reported. Most companies have a phishing email address you can forward these scam emails to.
- A new scamming strategy that is becoming more prevalent, caller ID spoofing, is a particularly dangerous one. In caller ID spoofing, scammers can trick your phone into displaying the phone number of a trusted contact like your bank, local government, or even your employer.
- Some red flags to be on the lookout for include the following:
- A sense of urgency, pressuring you to make decisions quickly to avoid further consequences
- Requests for payment, particularly if the payment method seems suspicious (wire transfer, gift cards, prepaid debit cards, etc.)
- Requests for personal information (Social Security number, passwords, mother's maiden name, account numbers, etc.)
- If you receive a call that seems suspicious, even if the number appears to have come from a legitimate source, do not answer any questions, especially ones that can be answered with "yes" or "no." Don't provide them with any personal information and certainly do not offer payment. Immediately hang up.
- If you're concerned that the call may have been legitimate, you can call the customer support number listed on that company or organization's official website or an account statement and explain that you received a call that seemed suspicious. If the call was legitimate, they will simply reconnect you to the right person or department - if not, you may have saved yourself a great deal of grief and money.
Keep Devices and Software Updated:
- Hardware and software companies are constantly rolling out updates with patches for security vulnerabilities. By keeping your devices updated, you ensure they always have the latest, most robust security features. Enable automatic updates to your devices whenever possible.
Trust Your Instincts:
- Your gut is oftentimes your most reliable line of defense - if something feels suspicious or too good to be true, it likely is.
- Pause, think, and ask a trusted friend, family member, you can even call us before proceeding.
- You will never regret being cautious.